OCR Advises Healthcare Groups to Carry Out Gap Analysis
In its April 2018 cybersecurity newsletter, OCR lauds the benefits of completing a gap analysis along with a risk analysis. The latter is required to discover risks and vulnerabilities that could potentially be exploited to gain access to ePHI, while a gap analysis helps healthcare groups and their business associates determine the range to which they are compliant with specific elements of the HIPAA Security Rule.
Completing a Risk Analysis
HIPAA requires covered groups and their business associates to perform a comprehensive, group-wide risk analysis to identify all potential dangers to the confidentiality, integrity, and availability of ePHI – 45 CFR § 164.308(a)(1)(ii)(A).
If a risk analysis is not completed, healthcare groups cannot be certain that all potential vulnerabilities have been discovered. Flaws would likely remain that could be exploited by threat actors to obtain access to ePHI.
While HIPAA does not state the methodology that should be employed when conducting risk analyses, OCR explained in its newsletter that risk analyses must contain certain factors:
- A thorough assessment of all dangers to all ePHI, regardless of where the data is created, received, maintained, or sent, or the source or location of ePHI.
- All locations and information systems where ePHI is formulated, received, maintained, or transmitted must be incorporated in the risk analysis, so an inventory should be established that includes all applications, mobile devices, communications equipment, electronic media, networks, and physical locations along with workstations, servers, and EHRs.
- The risk analysis should include technical and non-technical flaws, the latter includes policies and procedures, with the former concerned with software flaws, weaknesses in IT systems, and incorrectly configured information systems and security solutions.
- The effectiveness of existing controls must be assessed and documented, incorporating all security solutions such as AV software, endpoint protection systems, encryption software, and the use of patch management processes.
- The chances that a specific threat will exploit a vulnerability and the impact should a vulnerability be exploited must be reviewed and recorded.
- The level of risk should be estimated for any specific threat or vulnerability. With a risk level designated, it will be easier to determine the main priorities when mitigating dangers through the risk management process.
- The risk analysis must be recorded in sufficient detail to demonstrate that a thorough, organization-wide risk analysis has been conducted, and that the risk analysis was accurate and covered all locations, devices, applications, policies, and procedures including ePHI. OCR will request this documentation in the event of an investigation or compliance audit.
- A risk analysis is not a one-time process to ensure compliance with the HIPAA Security Rule – it must part of an ongoing process for continued compliance. The process must be constantly reviewed and updated, and risk analyses should be performed on an ongoing basis. HIPAA does not state how frequently a full or partial risk analysis should be completed. OCR suggests risk analyses are most effective when linked with a business processes.
Once a risk analysis has been completed, all risks and flaws identified must be addressed through a HIPAA-compliant security risk management process – 45 CFR § 164.308(a)(1)(ii)(B) – to reduce those risks to a reasonable and acceptable level.
Advice on conducting a group-wide risk analysis can be found on this link (HHS)
Gap Analysis Description
A gap analysis is not obligatory under HIPAA Rules, although it can help healthcare groups confirm that the requirements of the HIPAA Security Rule have been satisfied.
A gap analysis can be used as a partial assessment of an group’s compliance efforts or could cover all provisions of the HIPAA Security Rule. Many gap analyses could be performed, each assessing a separate set of standards and implementation specifications of the HIPAA Security Rule.
The gap analysis can give HIPAA-covered groups and their business associates a complete view of their compliance efforts, can help them discover areas where they are yet compliant with HIPAA Rules, and identify any gaps in the controls that have already been adapted.
Note that a gap analysis is not the same as a risk analysis, as it does not incorporate all possible risk to the confidentiality, integrity, and availability of ePHI as required by 45 C.F.R. §164.308(a)(1)(ii)(A).
OCR give this example of a simple gap analysis:
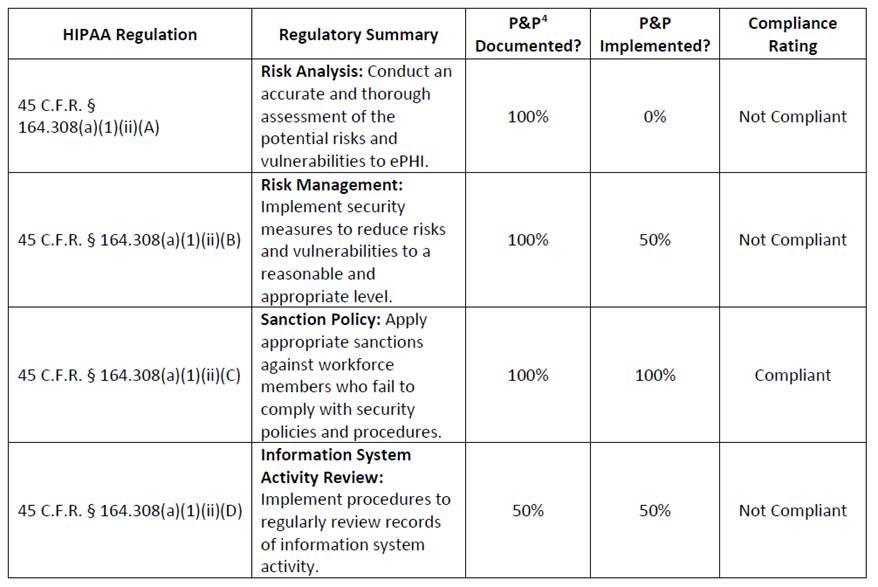
Source: OCR
